Building a Scalable BDD Automation...
November 12, 2025

When it comes to managing access and identities in the modern cloud landscape, Okta is a prominent player. Okta’s implementation of Role-Based Access Control (RBAC) enhances its identity and access management (IAM) platform, offering organizations a streamlined and secure way to manage user permissions across various applications and systems.
Okta’s RBAC is designed to simplify the management of user access by leveraging roles to control permissions across a wide range of applications and services. By integrating RBAC into its IAM solutions, Okta helps organizations enforce security policies and ensure that users have access only to the resources necessary for their roles.
Role Definition and Management: Okta allows organizations to define and manage roles based on job functions or departments. These roles can then be assigned specific permissions, streamlining the granting and modifying access process.
Automated Role Assignment: Okta’s platform supports automated role assignments based on department, job title, or location attributes. This automation reduces administrative overhead and ensures that users receive the correct access permissions as soon as they are onboarded.
Granular Permissions: Okta provides granular control over permissions, allowing organizations to specify exactly what actions each role can perform within an application. This fine-tuned control helps enforce the principle of least privilege, enhancing overall security.
Centralized Access Management: With Okta’s RBAC, organizations can manage access to both on-premises and cloud applications from a single, centralized platform. This unified approach simplifies administration and improves visibility into access controls.
Audit and Compliance: Okta’s RBAC includes robust auditing and reporting features, enabling organizations to track role assignments and changes. This visibility is crucial for compliance with regulatory requirements and for conducting security audits.
Enhanced Security: By implementing RBAC through Okta, organizations can ensure that users have access only to the resources they need, reducing the risk of unauthorized access and potential security breaches.
Improved Efficiency: Automated role assignment and centralized access management streamline the process of managing user permissions, allowing IT teams to focus on more strategic tasks.
Scalability: Okta’s RBAC is designed to scale with your organization, supporting both small businesses and large enterprises. As your organization grows, Okta can accommodate the increased complexity of user roles and permissions.
Simplified Compliance: With detailed audit logs and reporting capabilities, Okta’s RBAC helps organizations maintain compliance with various industry regulations and standards.
Become an Auth0 Developer First things first, let’s get you set up with an Auth0 Developer account. Head over to https://auth0.com/signup and sign up for free. This is your gateway to a suite of powerful authentication and authorization tools.
Create Your Web Application Once you’re in, it’s time to create your first Auth0 application. Navigate to the Applications section in your shiny new dashboard. Here, you’ll set up a web application with some specific configurations tailored to your needs.
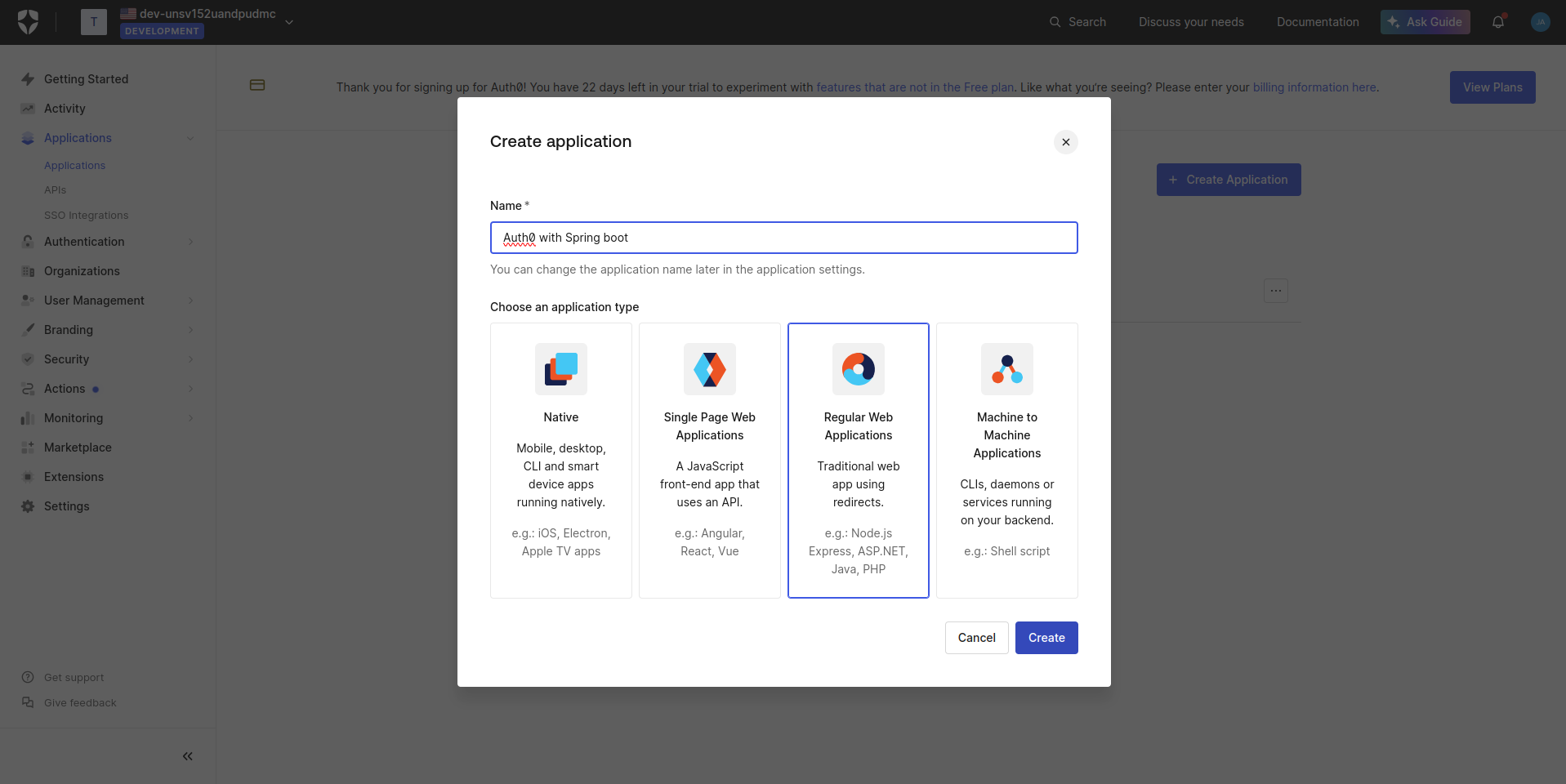
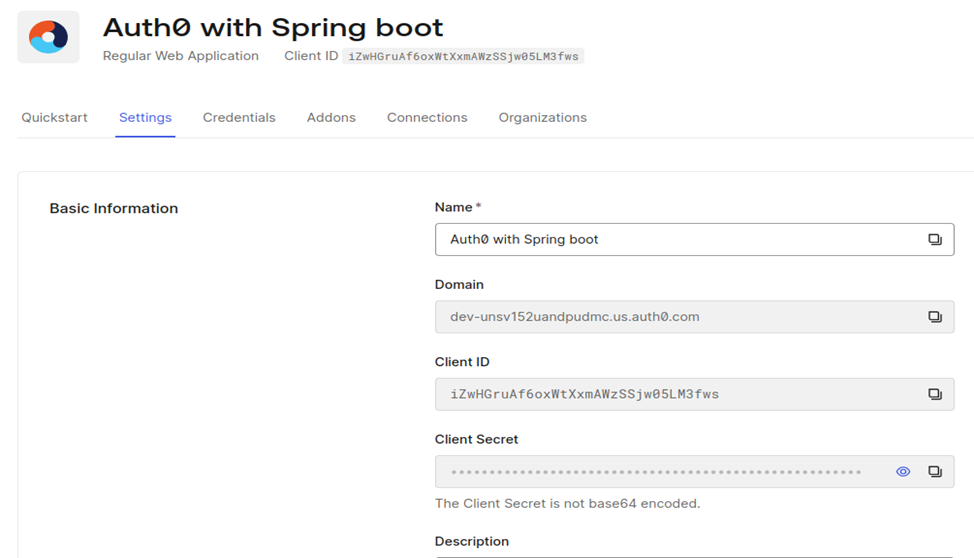
Now that you’ve created your Auth0 application, you’re about to receive two crucial pieces of information. Think of these as the keys to your digital fortress:
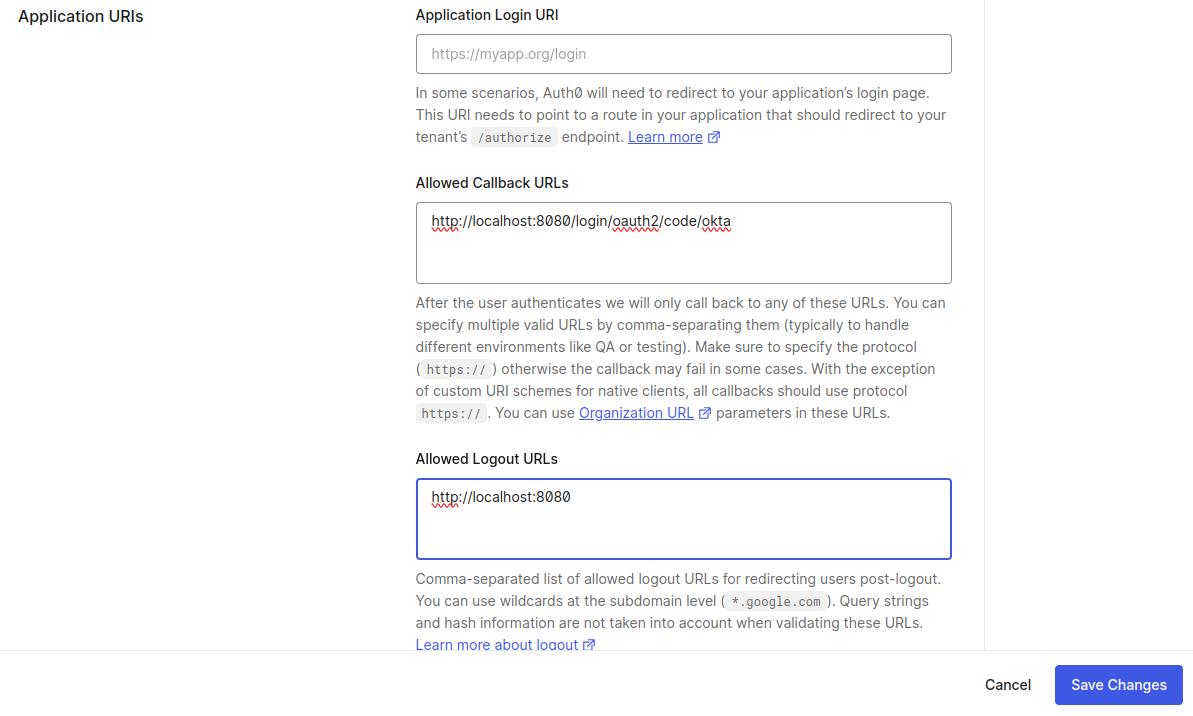
Now that we’ve got our basic setup, it’s time to tell Auth0 where our application lives. This step is crucial for establishing a secure connection between your app and Auth0’s authentication services.
As you navigate through your application settings, you’ll come across two important fields: Callback URLs and Logout URLs. These are the digital addresses where Auth0 will redirect users after they’ve logged in or out.
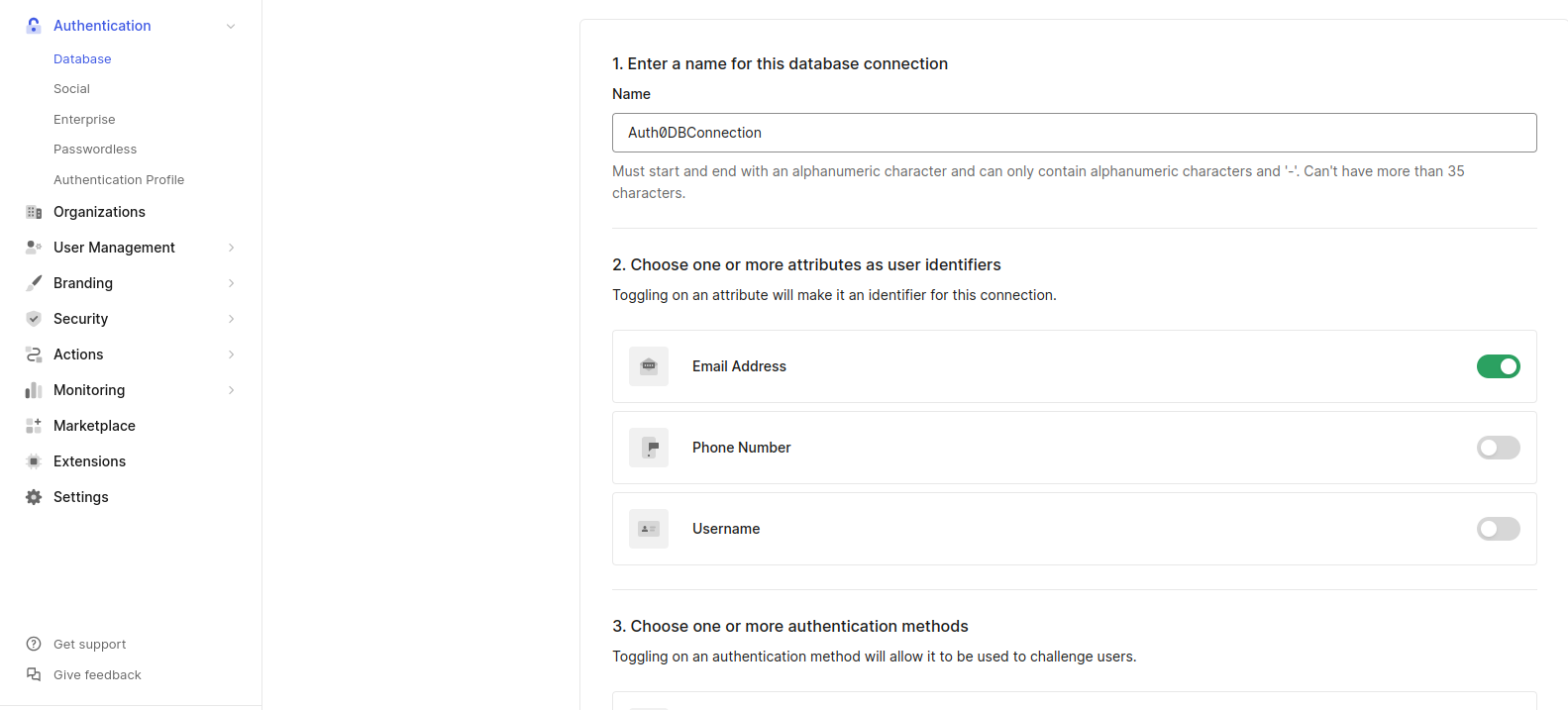
Now that we’ve got our application configured, it’s time to create a cozy digital home for our users’ information. Auth0 makes this process a breeze with its database connections feature. Let’s dive in!
Now that we’ve created our application and set up our user database, it’s time to connect these two vital components.
Look for the “Applications” Section This is where the magic happens! You’ll see a list of all your Auth0 applications.
Find Your Application Scan the list for the application we just created.
Toggle the Connection Next to your application’s name, you’ll see a switch. Flip it to the “On” position.
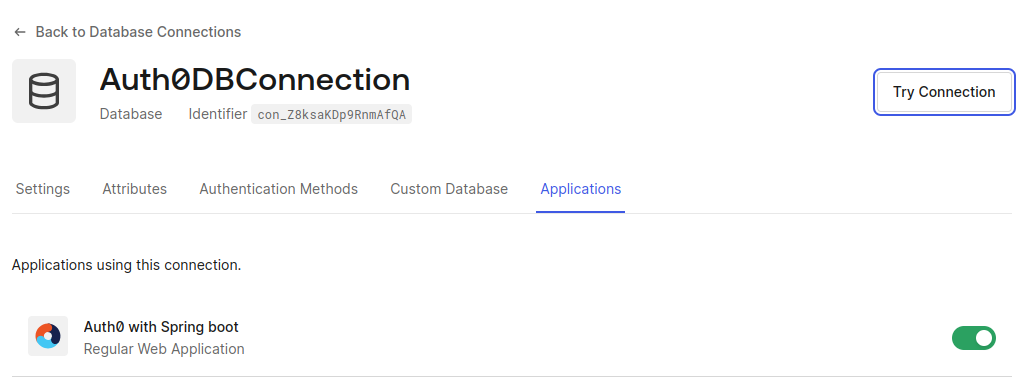
Now that we’ve set up our application and database, it’s time to breathe life into our system by creating our very first user.
Entering the User Management Hub Navigate to the “User Management” section and click on “Users.”
Click that inviting “Create User” button and prepare to bring a new member into your app’s ecosystem. As you fill out the form, remember to select the database connection we just created.
After creating the user, there’s one crucial step left – email verification.
Your new user is now in the system, but the journey doesn’t end here. Feel free to fine-tune their profile. Whether it’s setting preferences, assigning roles, etc.
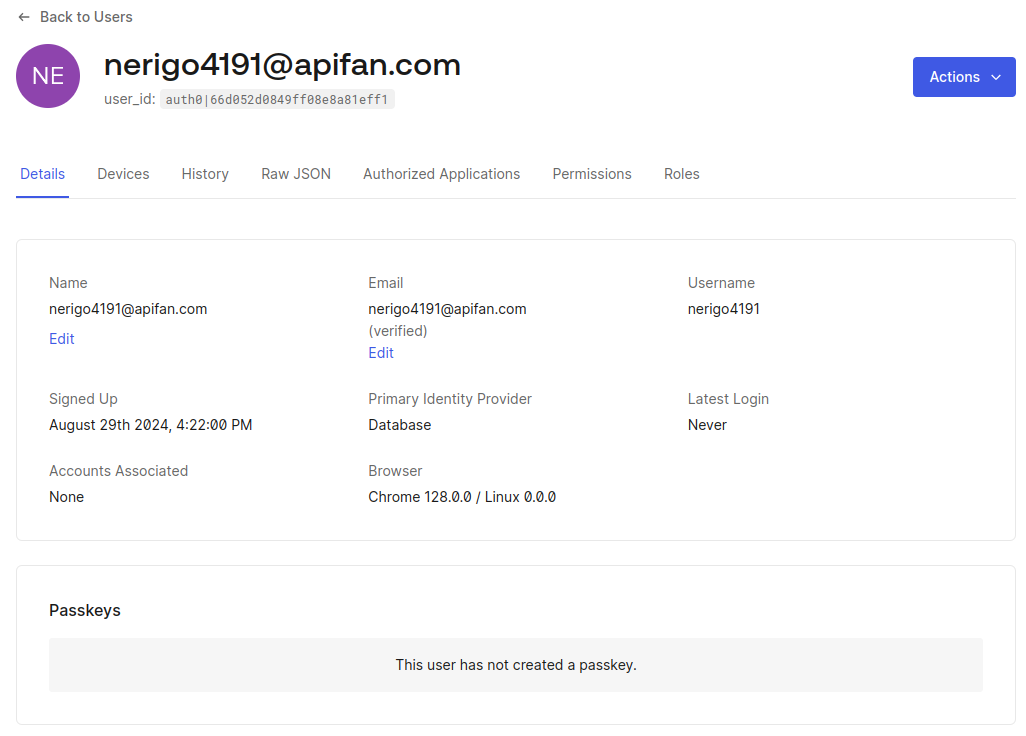
Now that we’ve brought our first user into existence, it’s time to add some structure to our digital society. Let’s explore the world of user roles – a powerful feature that allows us to define and manage user permissions with ease.
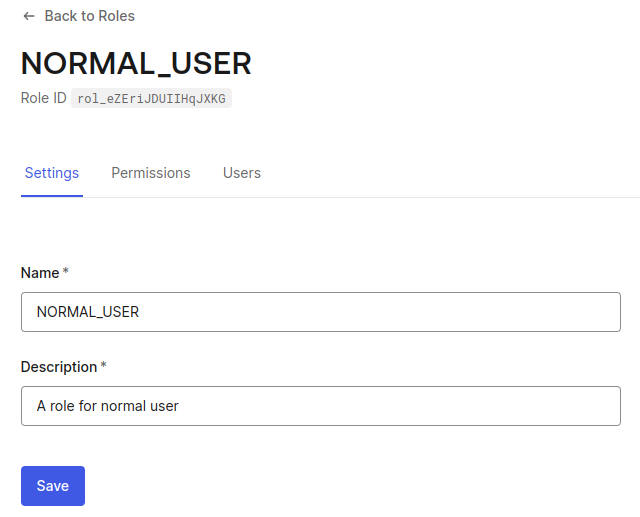
At the top of your screen, you’ll see a “Users” tab calling for your attention.
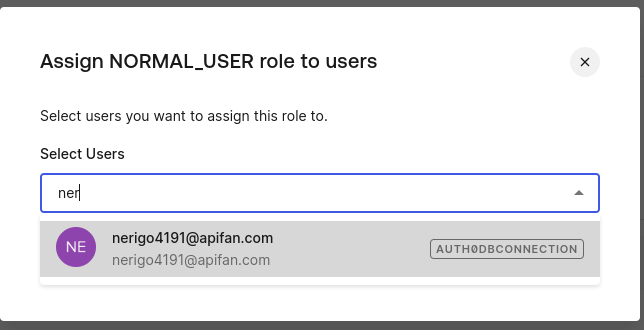
Select the user, assign the appropriate role, and ensure that the roles are incorporated into the login flow by navigating to Actions > Flows.
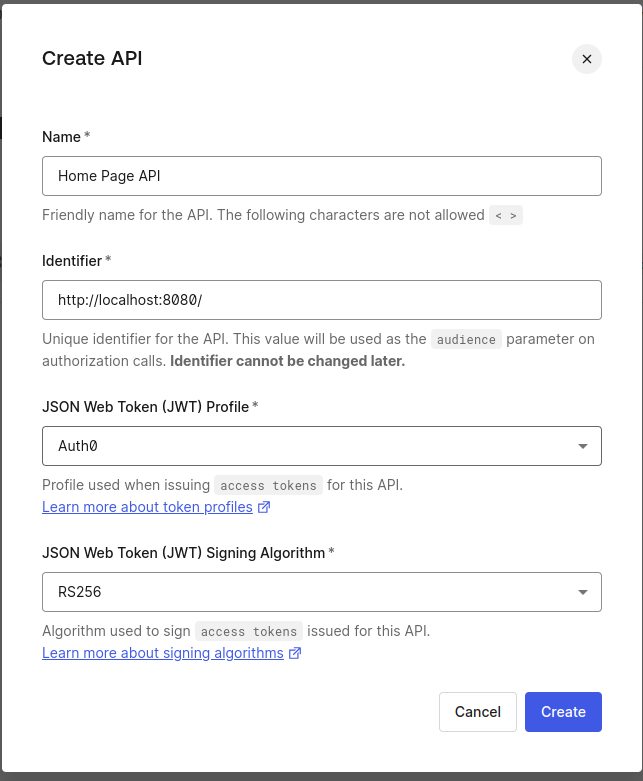
Navigate to Applications > APIs and create a new API. Assign a suitable identifier URL and configure Role-Based Access Control (RBAC) for the Home Page.
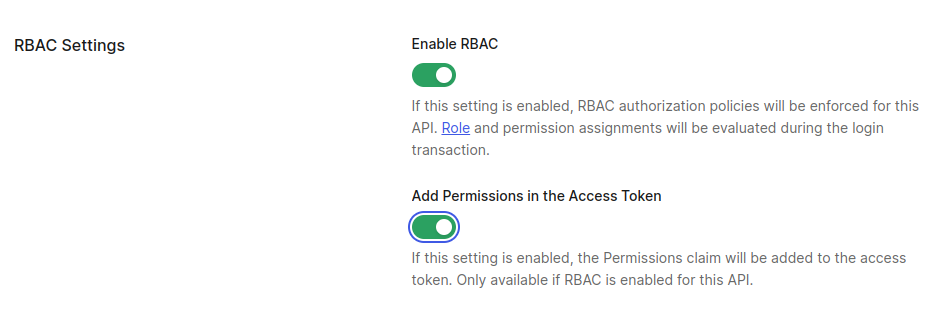
Access the API settings, enable RBAC, and save your changes.
Let’s create a Spring Boot starter application using spring.io:
Next, fill in all the project metadata and add the following dependencies:
Next, open the project in your preferred IDE and add the following configurations to the application.yml file:
To begin, update the client ID and secret as specified in the application you created in Auth0.
Next, you’ll need to set up a security configuration class to ensure that every incoming request is authenticated.
Launch your Spring Boot application. Once it’s running, open your web browser and navigate to http://localhost:8080. You’ll be automatically redirected to the Okta Single Sign-On (SSO) login page.
Log in using the credentials for the user you created earlier. Upon successful authentication (and authorizing the application if prompted), you will be redirected back to the home page of your Spring Boot application.
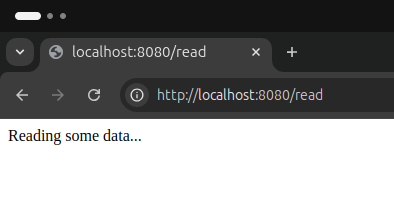
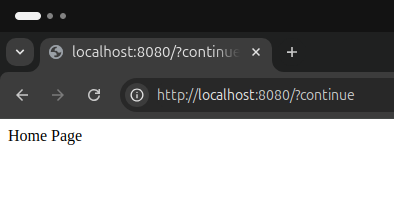
The home page is displayed as follows. Additionally, we can access the read endpoint at http://localhost:8080/read, thanks to the role we’ve assigned to the user.
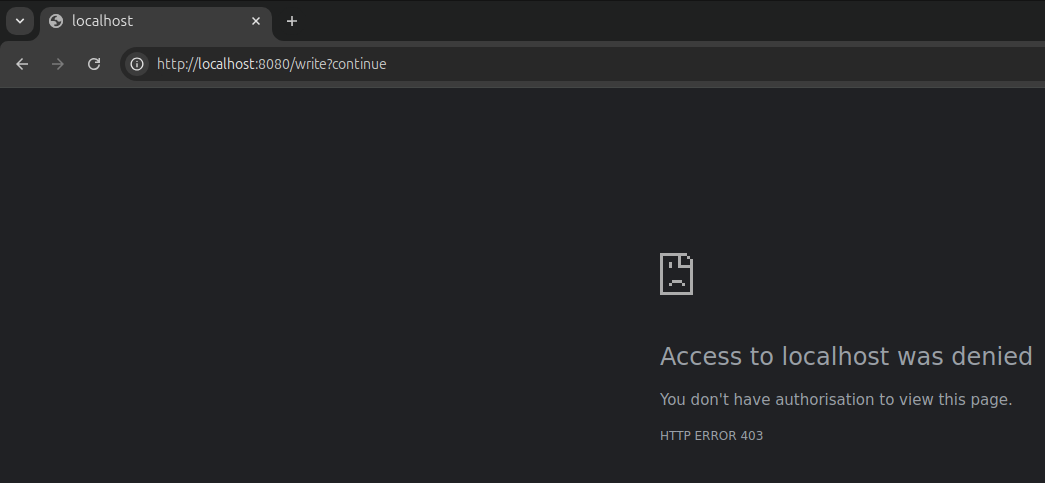
Unfortunately, we’re unable to access the write endpoint at http://localhost:8080/write because the admin role hasn’t been assigned to our user account.
In conclusion, integrating Okta’s Role-Based Access Control (RBAC) with Spring Boot offers a robust solution for managing user permissions and securing applications. Okta’s RBAC provides a granular approach to access management, ensuring that users only have the permissions necessary for their roles.
When combined with Spring Boot, it simplifies the implementation of security policies and enhances the overall security posture of your application. As a leading Java Spring Boot Development Company, we recognize that this synergy not only streamlines administrative tasks but also supports a more scalable and flexible security model, making it easier for organizations to maintain control and compliance in an increasingly complex digital environment.