
Oauth 2.0 is an authorization framework. OAuth 2.0 is a standard that enables an application or website to be an integrated resource maintained by other web apps on a user’s behalf. OAuth 2.0 stands for “Open Authorization.”
In this blog, we will discuss some of its alternatives.
What are the Alternatives of Oauth2.0
OpenID Connect, JSON Web Token, Amazon Cognito, and Keycloak are the most popular alternatives and competitors to OAuth2.
1. OpenID Connect

- It has been developed by extending OAuth 2.0.
- OpenId Connect is an authentication protocol that allows verifying of user identity
- In Oauth you get an access token, which will contain application claims.
- In OpenID Connect you will get an Access Token as well as an id_Token. Id_Token has the user’s claims, which allows the client to verify the identity of the user.
OAuth 2.0 is the foundation upon which OpenID Connect is based, and the OpenId Connect Specification has somewhat different terminology for the responsibilities in the flows:
- OpenID provider:
- The authorization server that generates the ID token is called the OpenID provider.
- end user:
- The end user’s information is contained in the ID token.
- relying party:
- The relying party is the client application that requests the ID token from Okta.
- ID token:
- ID token issued by the OpenID Provider and contains information about the end user in the form of claims.
- Claim:
- The claim contains details on the end user.
Grant Types:
OpenID Connect supports the following authentication flows:
- Implicit Flow:
- It is required for apps that have no “back end” logic on the web server, like a Javascript app.
- Authentication Flow:
- It is designed for apps that have a back end that can communicate with the IdP away from prying eyes.
- Resource Owner Password Grant:
- It does not have a login UI and is useful when access to a web browser is not possible.
- Client Credentials Grant:
- It is useful for machine-to-machine authorization.
Workflow of OpenId connect
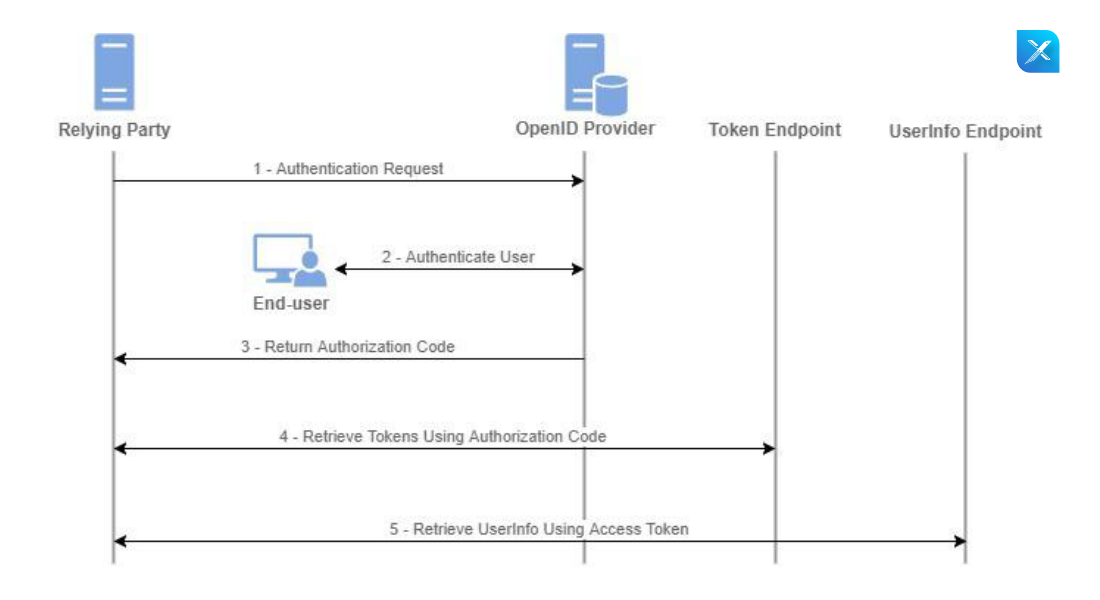
Step 1: In the first step, the user attempts to start a session with your client app and is redirected to the OpenID Provider, passing in the client ID, which is unique for that application.
Step 2: OpenID Provider authenticates and authorizes the user. It appears to follow the implicit flow thus far.
Step 3: OpenId Provider gives a one-time-use code and is passed back to the web server using a predefined Redirect URI.
Step 4: After that, the web server passes the code, client ID, and client secret to the OpenID Provider’s token endpoint, and the OpenID Provider validates the code and returns a one-hour access token.
Step 5: The client uses the access token to get further details about the user and establishes a session for the user.
Benefits :
- By using OpenID Connect, you may map an OpenID user on the provider site with any data your app or website keeps on that user instead of having to store user login information within your own database systems.
- The OpenID approach is more lightweight than the hybrid auth implementation.
Drawbacks:
- OpenID Connect is simply an authentication service for verifying a user account state, not an authorization system like OAuth, which allows an application or service to perform actions on the user’s behalf once authorized.
- This means that a straightforward OpenID integration won’t be able to send signed requests to the provider site in order to obtain, change, or remove a user’s social information.
2. Keycloak

- Keycloak is an open-source identifier and access management solution targeted at modern applications and services.
- It offers features such as Single-Sign-On, User federation, Client Adapters, Admin console, and Account management console.
- When a user authenticates with a keycloak then individual applications do not have to deal with login forms and the authentication process of users.
- The same thing applies to logout, Keycloak offers Single-Sign-Out which means users will only have to log out once and it will be logged out from all applications that use Keycloak.
- Keycloak is based on a standard protocol, it provides support for multiple protocols such as OpenID Connect, Oauth 2.0, and SAML.
Workflow of keycloak
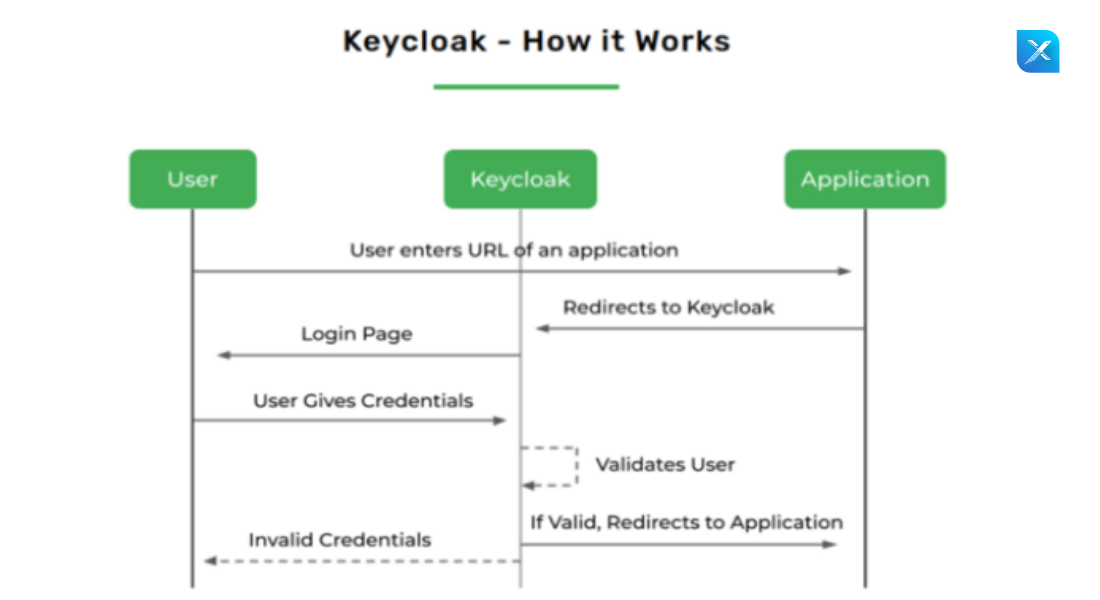
Step 1: When a user navigates to the application, they are first redirected to the Keycloak authentication page.
Step 2: After adding login credentials, Keycloak will redirect the user to the application with the code.
Step 3: The application will exchange this code with an ID and access token and it will be used to identify users.
Benefits:
- It is faster to setup keycloak
- It is especially true for bigger applications with complex user modules.
- It is ready to adopt a new authentication mechanism
- It offers a web-based GUI that facilitates configuration updates.
Drawbacks:
- It has complex architecture.
- Difficult to understand.
- It has a higher learning cost because of some Chinese materials.
3. Amazon Cognito
- Amazon Cognito is an Amazon Web Service Product that controls user authentication, authorization, and user management for mobile applications on internet-connected devices.
- Here users can directly log in with credentials through third parties such as Facebook, Amazon google, and apple.
- It is a simple user identity and data synchronization service that helps to manage and synchronize app data for users securely across mobile devices.
Amazon Cognito is composed of two primary parts.
- 1. User pool — It is user directories that provide sign-up and sign-in options for apps.
- 2. Identity pool — It enables you to grant your user access to other AWS services.
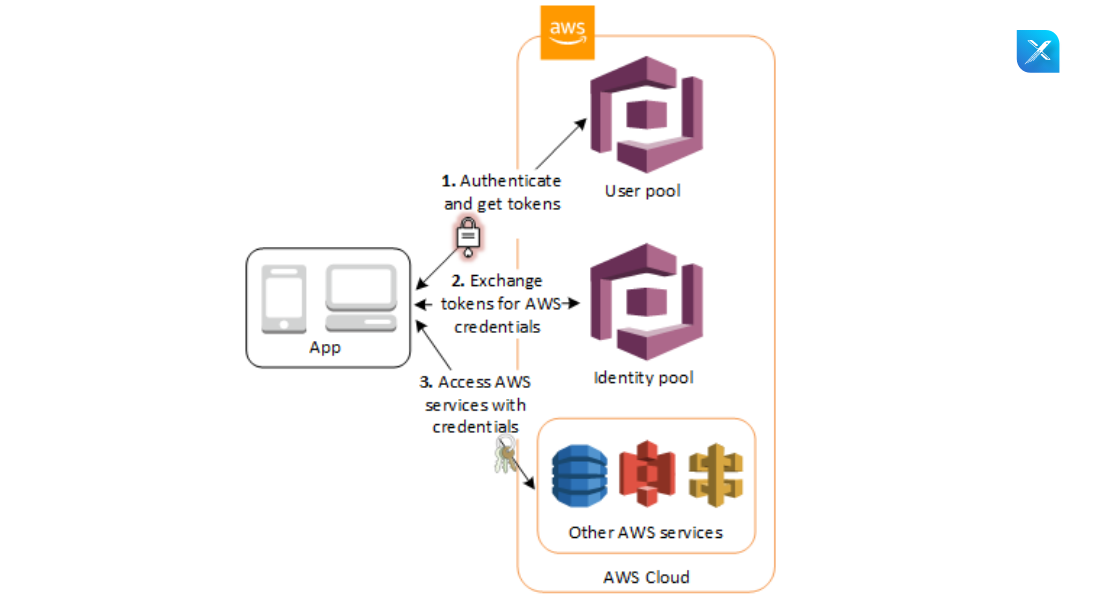
Step 1: The app user signs in with the user pool
Step 2: Once successfully authenticated, they receive a user pool token.
Step 3: The app exchanges the user pool tokens for AWS credentials through the identity pool.
Step 4: Now app users can use these AWS credentials to access other AWS services such as Amazon S3 or DynamoDB
Benefits
- It provides simple integration.
- It has reliable sign-in features.
- Password is securely stored in a database
Drawbacks
- It’s difficult to use — Amazon Cognito can be quite confusing to set up and use, particularly for developers unfamiliar with AWS.
- It’s pricey – Using Amazon Cognito for additional users or applications will increase the cost of the service significantly.
- It depends on AWS; if there are issues with AWS, there may be issues with Amazon Cognito as well.
4. JSON Web Token
- A JSON object can be used to securely transport information between parties thanks to the open standard known as JSON Web Token.
- The fact that this information is digitally signed allows for verification and confidence.
Structure Of JWT
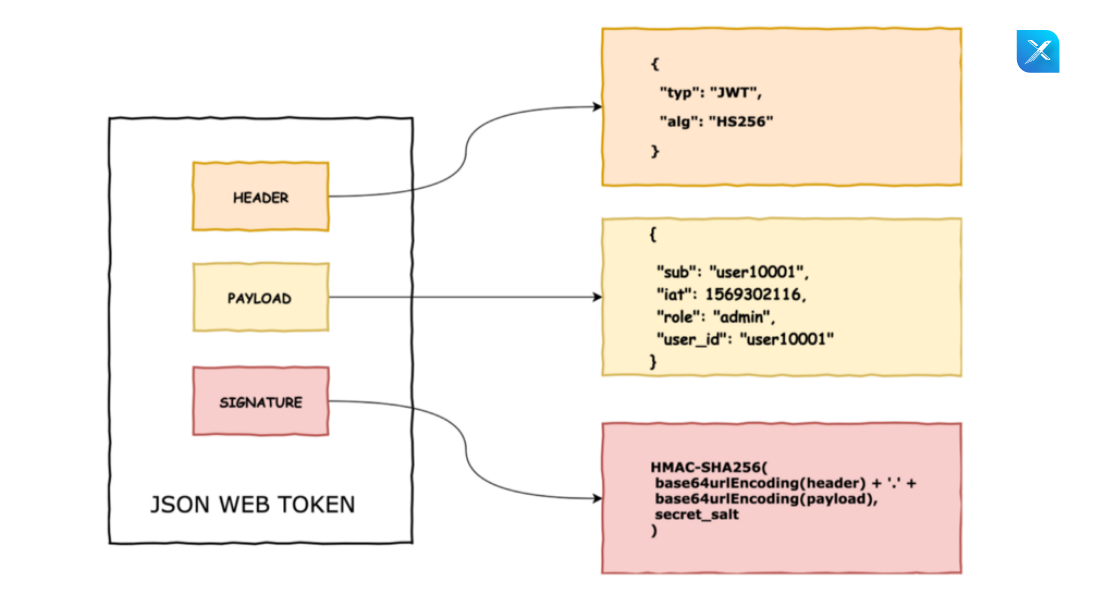
A JSON Web Token is composed of three parts, each separated by a dot (. ):
A JWT typically looks like the following.
xxxxx.yyyyy.zzzzz
Let’s break down the different parts.
Header :
The type of the token, which is JWT, and the signing technique being used, such as HMAC SHA256 or RSA, are both included in the header.
For example:
{
“alg”: “HS256”,
“typ”: “JWT”
}
Payload :
The payload, which includes the claims, makes up the token’s second component. Claims are assertions about a subject and additional information.
An example payload could be:
{
“sub”: “1234567890”,
“name”: “John Doe”,
“admin”: true
}
The second component of the JSON Web Token is the payload, which is then Base64Url encoded.
Signature:
You must sign the encoded header, encoded payload, secret, and algorithm indicated in the header to construct the signature portion.
If you choose to utilize the HMAC SHA256 algorithm, for instance, the signature will be generated as follows:
HMACSHA256(
base64UrlEncode(header) + “.” +
base64UrlEncode(payload),
secret)
When a token is signed with a private key, it can also confirm that the sender of the JWT is who they claim to be. The signature is used to ensure that the message wasn’t altered along the way.
Workflow of JSON Web Tokens
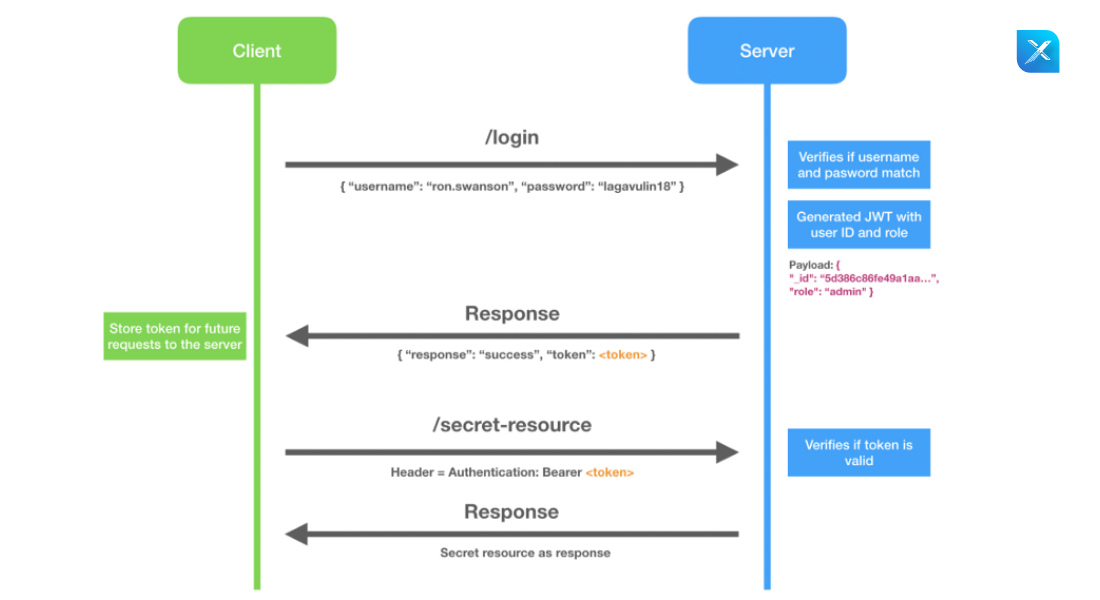
Step 1: User sign in using username and password.
Step 2: The authentication server verifies the credentials and issues a JWT signed using a private key.
Step 3: Moving forward, the client will use the JWT to access protected resources by passing the JWT in the HTTP Authorization header.
Step 4: The resource server then verifies the authenticity of the token using the public key.
Benefits:
- JWT tokens are stateless in that session data is not kept on the server, which reduces the need for server RAM.
- To verify the legitimacy of the source, JWT tokens are utilized.
- Receivers can check data signing to see if the source of the token is legitimate.
Drawbacks:
- whenever a user account needs to be removed In the case application has to wait for the token to expire for the user account deactivation
- Since no refresh tokens are supplied in their implementation, JWT tokens require re-authentication after they expire.
- When account hijacking happens, a user may need to change their password ASAP. But with JWT if authentication is done beforehand, then a token generated for the previous password would still be valid even after the user password is changed until the expiry time.
Wrapping Up
Above mentioned alternatives can be a boon for you as a Java developer. Grants in OAuth 2.0 are the series of actions a Client must do to obtain resource access authorization. The authorization framework offers a variety of grant types to handle various scenarios.







